In today’s fast-paced business environment, the need for efficient and accurate workflow automation is more pressing than ever. With advancements in AI, several approaches have emerged to address automation challenges, including Robotic Process Automation (RPA), AI-native platforms, and Agentic frameworks. While each has its merits, at artiquare, we believe the Mixture of Experts (MoE) framework is uniquely positioned to handle the complexities of modern workflows with unparalleled precision and efficiency.
The Growing Complexity of Workflow Automation
As businesses scale and operations become more complex, the demand for sophisticated automation solutions increases. Traditional methods like RPA have been instrumental in streamlining repetitive tasks, but they often fall short when dealing with multifaceted workflows that require dynamic decision-making and adaptability.
AI-native platforms have brought significant advancements by embedding AI directly into applications, allowing for more intuitive and efficient task completion. However, even these platforms can struggle with consistency when managing workflows that involve multiple steps and complex decision trees.
The introduction of Agentic frameworks, where AI agents simulate human decision-making, has added another layer of capability to the automation landscape. These frameworks offer greater flexibility but can be difficult to scale effectively, especially in environments with intricate and evolving workflows.
The Case for Mixture of Experts (MoE)
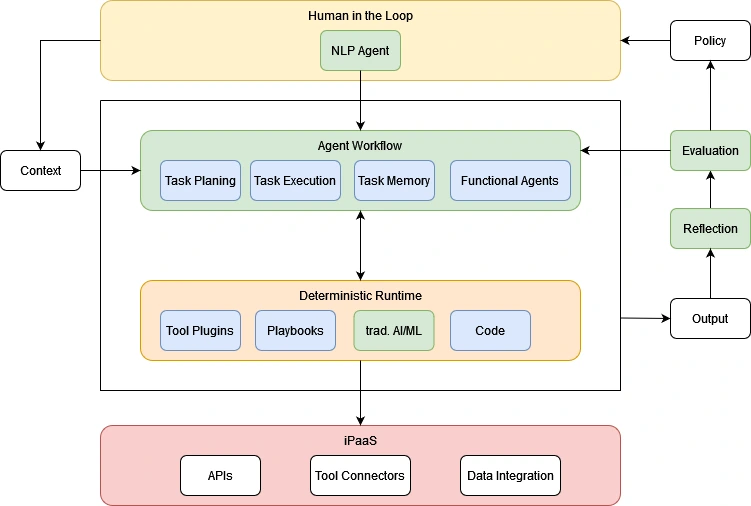
In response to these challenges, the Mixture of Experts framework offers a transformative solution. Mixture of Experts deconstructs complex workflows into specialized tasks, each managed by a dedicated AI agent. These agents are supported by a robust “scaffolding” of tools, data, and interfaces that optimize their performance for each specific task.
Why MoE Stands Out
- Specialized Task Handling: By breaking down workflows into distinct tasks, MoE ensures that each task is managed by the most suitable AI agent. This specialization leads to more accurate and efficient outcomes, particularly in workflows that require a high degree of precision.
- Deterministic Outcomes: A key challenge in automation is ensuring that workflows yield consistent and reliable outcomes. MoE addresses this by synthesizing outputs from various tasks in a deterministic runtime, ensuring that the final output is both consistent and accurate. This is especially critical in industries where precision is non-negotiable, such as enterprise automation software, high-automation manufacturing, industrial robotics, and finance.
- Human-in-the-Loop Oversight: The Mixture of Experts framework incorporates a “Human-in-the-Loop” interface, allowing real-time interaction and refinement of tasks. This ensures that the automation process is not only accurate but also adaptable to changes and unforeseen variables. By involving human oversight, businesses can maintain a level of control over automated processes, ensuring that AI-driven decisions align with business goals and standards.
- Flexibility and Scalability: As business needs evolve, automation processes must be flexible enough to adapt. MoE’s modular approach allows for reconfiguration and upgrades as needed, making it a scalable solution that can grow alongside your business. Whether scaling operations or introducing new workflows, Mixture of Experts provides the flexibility needed to accommodate change without sacrificing efficiency or accuracy.
Real-World Applications of Mixture of Experts
At artiquare, we have implemented the MoE framework in several pilot projects across various industries. These projects have not only demonstrated the framework’s versatility but also its ability to deliver reliable and efficient automation solutions in complex environments.
- IT Service Management (ITSM): In IT service management, MoE has been instrumental in automating customer service workflows, reducing response times, and improving service accuracy.
- Insurance: The insurance industry has benefited from MoE’s ability to handle complex claim processing tasks, ensuring that each step is executed with precision, leading to faster and more accurate claim resolutions.
- Sky Computing: We are currently developing a self-service portal for a sky computing company, where Mixture of Experts enables users to manage cloud resources efficiently through automated workflows.
- Research Assistance: Our MoE-powered research assistant tool automates data gathering, analysis, and reporting tasks, significantly reducing the time and effort required for comprehensive research.
These examples illustrate the broad applicability of the MoE framework and its potential to revolutionize workflow automation across industries.
Our Pilot Project and MVP
Building on the success of our pilot projects, we are excited to introduce our upcoming MVP, which will showcase the capabilities of the MoE framework in real-world scenarios. This MVP will demonstrate how MoE can be applied across various industries to enhance workflow efficiency, accuracy, and scalability.
Through our pilot projects, we have seen firsthand how the Mixture of Experts framework can bridge the gaps left by traditional automation methods, offering a more robust and adaptable solution for complex tasks. As we prepare to launch our MVP, we are eager to share the potential of MoE with our clients and the broader business community.
The Future of Workflow Automation
The Mixture of Experts framework represents a significant leap forward in the field of workflow automation. By harnessing the power of specialized AI agents, MoE offers a scalable, flexible, and precise solution for automating even the most complex workflows.
As AI continues to evolve, we believe that MoE will play a critical role in shaping the future of workflow automation. At artiquare, we are committed to staying at the forefront of these advancements, ensuring that our clients benefit from the most effective and innovative solutions available.
For those interested in exploring the broader trends in AI-driven automation, we recommend reading this insightful article from Insight Partners, which discusses the evolution of automation platforms and the role of AI in transforming workflows.
Stay tuned to our blog for updates as we continue to explore the potential of MoE and its impact on the future of automation.





